En lien direct avec le billet d’hier, j’ai donc concocté un script permettant d’automatiser les modifications requises en base de registre pour l’activation de TLS 1.2 au profit de TLS 1.0 et 1.1.
Naturellement, le script est à exécuter avec un compte d’utilisateur ayant les droits d’écrire en base de registre.
echo "This script will create or write over some registry keys related to TLS 1.0, TLS 1.1 and TLS 1.2 - make sure to be aware of the effect of those modifications."
$continue = Read-Host "Are you sure you want to execute this script ? Type 'Y' to continue or any other character to abort"
if ($continue -ne 'Y') {break}
$pathtls10 = "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0"
$pathtls11 = "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1"
$pathtls12 = "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2"
$pathprtcl = "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\"
echo "Creating TLS keys..."
New-Item -Path $pathprtcl -Name "TLS 1.0" -Force | Out-Null
New-Item -Path $pathprtcl -Name "TLS 1.1" -Force | Out-Null
New-Item -Path $pathprtcl -Name "TLS 1.2" -Force | Out-Null
New-Item -Path $pathtls10 -Name "Server" -Force | Out-Null
New-Item -Path $pathtls10 -Name "Client" -Force | Out-Null
New-Item -Path $pathtls11 -Name "Server" -Force | Out-Null
New-Item -Path $pathtls11 -Name "Client" -Force | Out-Null
New-Item -Path $pathtls12 -Name "Server" -Force | Out-Null
New-Item -Path $pathtls12 -Name "Client" -Force | Out-Null
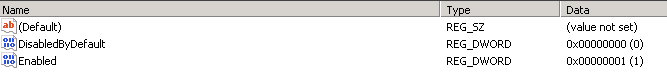
echo "Adding DWORD properties..."
New-ItemProperty -Path $pathtls10Client -PropertyType DWORD -Name "DisabledByDefault" -Value "0x00000000" -Force | Out-Null
New-ItemProperty -Path $pathtls10Server -PropertyType DWORD -Name "DisabledByDefault" -Value "0x00000000" -Force | Out-Null
New-ItemProperty -Path $pathtls11Client -PropertyType DWORD -Name "DisabledByDefault" -Value "0x00000000" -Force | Out-Null
New-ItemProperty -Path $pathtls11Server -PropertyType DWORD -Name "DisabledByDefault" -Value "0x00000000" -Force | Out-Null
New-ItemProperty -Path $pathtls12Client -PropertyType DWORD -Name "DisabledByDefault" -Value "0x00000000" -Force | Out-Null
New-ItemProperty -Path $pathtls12Server -PropertyType DWORD -Name "DisabledByDefault" -Value "0x00000000" -Force | Out-Null
New-ItemProperty -Path $pathtls10Client -PropertyType DWORD -Name "Enabled" -Value "0x00000000" -Force | Out-Null
New-ItemProperty -Path $pathtls10Server -PropertyType DWORD -Name "Enabled" -Value "0x00000000" -Force | Out-Null
New-ItemProperty -Path $pathtls11Client -PropertyType DWORD -Name "Enabled" -Value "0x00000000" -Force | Out-Null
New-ItemProperty -Path $pathtls11Server -PropertyType DWORD -Name "Enabled" -Value "0x00000000" -Force | Out-Null
New-ItemProperty -Path $pathtls12Client -PropertyType DWORD -Name "Enabled" -Value "0x00000001" -Force | Out-Null
New-ItemProperty -Path $pathtls12Server -PropertyType DWORD -Name "Enabled" -Value "0x00000001" -Force | Out-Null
echo "Done."
$reboot = Read-Host "Server has to reboot in order to apply the modifications made. Type 'Y' if you want to start a reboot countdown of 2 minutes."
if ($reboot -ne 'Y') {break}
shutdown -r -t 120
echo "Server will reboot in 2 minutes."
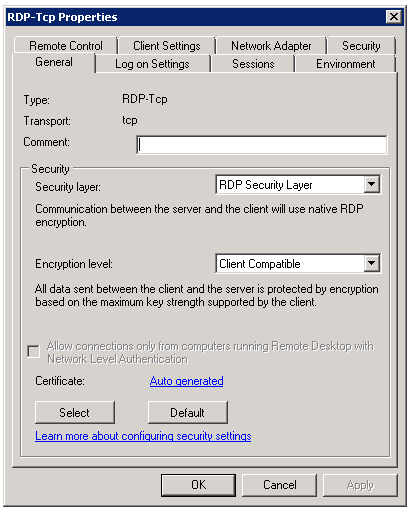
Si jamais l’accès Terminal Server est impossible au redémarrage, il faut contrôler les réglages de sécurité du serveur RDP et être sûr que le KB3080079 est installé si l’OS est Windows Server 2008 R2. Tout est expliqué dans l’article que j’ai publié hier sur les manipulations d’origine.